Check Point Releases Full Disk Encryption For Mac
- Upgrade gives a seamless migration to the new Native Encryption Management. The disk is encrypted at all times. For more information on Check Point releases see: Maintrain. Map, Maintrain Releases plan. For more information on the Enterprise Endpoint Security E80.71 Client, see: sk115655: Check Point Capsule Docs E80.71 Mac Standalone.
- The Check Point Full Disk Encryption Software Blade provides automatic security for all information on endpoint hard drives, including user data, operating system files and temporary and erased files. For maximum data protection, multi-factor pre-boot authentication ensures user identity, while encryption prevents data loss from theft.
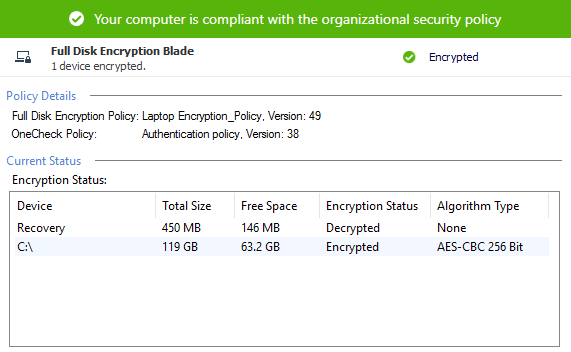
May 28, 2008 Check Point Software Technologies Ltd. Today announced the release of Check Point Full Disk Encryption for Mac OS X, the industry’s first full-disk encryption solution with pre-boot.
We make use of Checkpoint right here, and are usually presently in the procedure of planning a main from the standalone client to the full console version. They had some issues in the recent with the Operating-system A and Home windows versions not becoming in sync, but with thé most recent release Elizabeth80 release, the clients are similar. There are still a few gaps, such as not really supporting Blend runs, but overall, things have become excellent.
Deployment provides been simple: We create a composer deal that pushes the installer and our set up profile onto the client, and then call a script to run through thé pkg installer. lt offers worked perfectly for us. Simply because much as management goes, the cause we are relocating to the gaming console version is usually to have got better revealing. Presently, the encryption files are composed to a File share, and that can be all the logging we get.
We use the JSS' EA to get a more up to time picture, but with the Gaming console edition, it allows for more 'current' up-dates (1-2 minutes). The balance has ended up great for us. We have discovered a few iMacs that delivered to us with poor obstructions/sectors that had been not selected up by ány of óur HD diagnostics. Whén we have got achieved out to help, they have been quick to respond. Like I mentioned above, I certainly recommend the internet chat as the best option.
Reliability has happen to be pretty good. We noticed an uptick in 'black screens' that leave the machines in an un-bootable state, but that is usually more credited to the reality that these pushes have ended up encrypted for 4-5 years, and are utilized 24/7. As far as performance goes, we have noticed that with Checkpoint we are obtaining about a 1-2% performance hit over FileVault, but nothing at all that provides cause main problems. We are just wrap up a proof of idea with Checkpoint for Mac and of the choices out there I'n state it is by significantly the best. Specifically if you integrate with AD. The encryption can be pretty quick with low overhead after the fact. Deployment is usually really simple ánd its in their róadmap to end up being capable to develop Mac packages from the system.
With SRS Audio Essentials, the next generation of SRS audio software for Mac has arrived!! Audio Essentials is downloadable software that delivers home theater quality sound on your Mac. SRS Audio Essentials is fully customizable and works with virtually all media players and content service. Audio essentials download for mac.
The two biggest offers for me on the product are usually the preboot single indication on THAT WORKS and the capability of our technicians to mount the filesystem whiIe booted from oné of our crisis turns. This gives it párity with FiIeVault, which we cán not deploy in our environment. I've been examining it for about a month if you have any particular questions. Sony vaio vgn cs11s drivers for mac.
@iJake That will be 100% correct. There are usually some factors you can do to reduce this, using users to secure down the 'Security Personal privacy' choice pane arrives to brain. But, in the end, you are usually right.
If someone provides an administrative accounts, that is also authorized to open the travel, and wants to decrypt the commute, they can. That said, any of the various other solutions allow an management accounts that is usually certified to open the commute to access, and copy information off of, the encrypted get - which will be the root of what you're attempting to avoid. There is certainly a great deal of have confidence in/responsibility given to people that possess administrative rights to a device, this is no different. I deal with this as an issue with busting corporate policy. Established up a sensible team for machines that are usually not really encrypted and have got it mail you on group change. If someone decrypts their machine, provide them a pretty firm caution and re-encrypt the push. If it happens again, forward the e-mail to your protection group or Human resources and let them talk about the worker's continued potential at the corporation.
Wé didn't Symantec bécause If I'michael remember properly it offers the serious design downside of not being capable to possess the device close down during preliminary encryption. It would split the encryption. Symantec bought PGP, therefore if you're also familiar with that then its what it is. Apart from Gate and FileVault we examined Credant and McAfée. The Credant had some issues when I very first examined it but after those were eliminated up it proved helpful pretty nicely. It simply doesn'testosterone levels present pre boot and that was a simply no set off for me.
We use Credant file encryption on our PCs and are quite experienced with it. Its definitely the greatest option if you want the total least switch for your clients. McAfee is just not prepared on the Macintosh. It can't function with nearby users for pre shoe but rather they HAVE to become AD. That eliminates any regional admin accounts you might use. As nicely, there is usually no method to attach the filesystem from another push. I wasn't actually a enthusiast of the ePO console as its quite complicated and overcomplicated.
I make use of Symantec Encryption Desktop computer or PGP. I can provide a checklist of reasons that you might not want to use it. It requires over the Apple company recovery partition and makes it really tough to boot to another partitión although bootcamp supposedly works.
Getting User Data on a different partition is definitely possible but like i said you cannot boot to another OS partition or restore only the OS partition in my several attempts anyway therefore there will be no point in separating user data from the Operating-system. Filevault is definitely not much better for multi-partition things either, I discovered some device some actually smart guy had written to install the consumer data partition, which has to become encrypted separately and installed separately and it works almost all of the period, but every today and after that i login and the user data partition do not attach, its an easy repair to reboot but kind óf clunky. It is usually very good at finding bad areas on the disk, the bad news will be it usually does not really shoe when it discovers them.
It can be very susceptible to OS X up-dates, read this mainly because might not really shoe after an up-date. It only supports 8 keyboard layouts fully, others mainly function but the UK is not really one of the backed layouts and if you make use of the pound sign in your passphrase you are heading to have a bad day time. It encrypts a SSD actually quick, and the later on version encrypts a little bit quicker on the rotating disks, but 320GW in about 12 hrs is usually what I discover and you cannot use the machine during this period on rotating disks because it is usually so gradual. Some firmware up-dates seem difficult to set up because I think the recuperation partition and firmware stuff is taken over by shoe safeguard. The shoe guard password has to end up being managed individually from the user password.
Good or bad you choose, it does not really autologin after you type your boot guard password. Good things a consumer cannot decrypt their drive without herculean efforts.
As soon as its there it will not appear to affect the techniques overall performance, we depart that to SEP. Having PGP installed on a customers computer does obtain them all to end up being pretty diligent about hooking up their period device backup disks regularly. In all significance though, i have got near 1000 users on PGP, we possess got a couple dozen or therefore over the final calendar year that possess gotten the zero boot mark, and can that all become held responsible on PGP?
The devices were changed and the techniques ran great after. From my expertise at some other balances that might end up being a little bit higher for disk failure although every laptop with a 7200 rpm travel i have got ever experienced has ended up changed. I will be starting a couple of tasks for a few of new customers with Checkpoint quickly so I feel happy to see the good testimonials on it.